Here is an example of SSH tunnel setup inside a couple of SSH tunnels to create an all encrypted connection.
The setup is shown in the picture below:
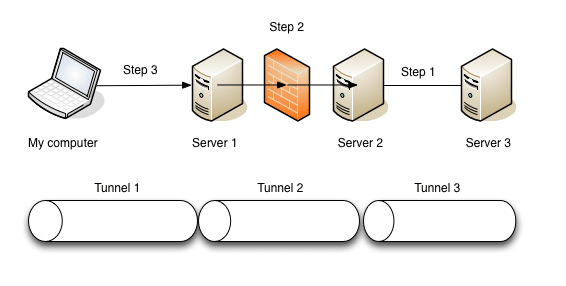
The following rules apply:
- Server 1 is public
- Server 2 can only be accessed through Server 1
- Server 3 can only be accessed through Server 2
- All Servers have a SSH server running
- My computer has only an SSH client
To set this up we start with the “small” tunnels:
Step 1
Set up Tunnel 3 with the following command:
ssh -N -L 2000:localhost:22 user@Server3
This creates a persitent (-N option) port forwarding from port 22 on Server 3 and to port 2000 on Server 2
Step 2
Set up Tunnel 2 between Server 1 and Server 2 with this command:
ssh -N -L 3000:localhost:2000 user@Server2
This sets upp a persistent tunnel between port 2000 on Server 2 and to port 3000 on Server 1
Step 3
Set up my connection (Tunnel 1) to the tunnel on Server 1 (the tunnel which is going all the way to Server 3)
ssh -N -L 4000:localhost:3000 user@Server1
This sets up a persistent tunnel between port 3000 on Server 1 and to port 4000 on My Computer
All the “small” tunnels are done!
Now we create a tunnel inside these tunnels to keep the connection secure:
ssh -p 4000 -N -L 8080:localhost:80 -o HostKeyAlias="Server3" user@localhost
This creates a tunnel from port 80 on Server 3 to port 8080 on My Computer. Lets take a closer look:
- -p 4000 – we start a new tunnel by connecting to port 4000 on My Computer (see port 4000 in last step above). This means that we are connecting through the tunnel we setup to Server 1 (that is connected to Server 2 – that is connected to Server 3)
- 8080:localhost:80 – we are forwarding port 80 on Server 3 to port 8080 on My Computer
- HostKeyAlias=”Server3″ – this is often needed since the new tunnel should authenticate with Server3 and not My Computer. Failing to provide this may lead to “Man-in-the-Middle” attack warnings and failure to log on Server 3
- user@localhost – localhost in this case is actually Server 3 so use your Server 3 credentials here
To add more tunnels just use the last command and define new ports to forward. As soon as the “small” tunnels are setup you can reach any open port on Server 3 for a tunnel
Not easy but now at least I have something to start with 🙂

